X & Google Lite Accounts
For the full documentation, visit the GitLab repo.
Disclaimers
⚠⚠ IMPORTANT DO NOT SKIP ⚠⚠
While LeoInfra V2 has been in production on INLEO for quite some time, consider this as Beta technology. Implementing this technology is done so at your discretion as an application owner. We also advise ample displays giving users proper education and warnings about key handling.
X & Google Lite Accounts (Lite Account, Web2 Authentication)

X & Google Lite Accounts offer A LOT of convenience for new users. HOWEVER, a big caveat of Lite Accounts is - as the name suggests - they are LITE accounts. These accounts are not full self-custody and they rely on the LeoInfra server (or your infra, if you choose to clone our Open Source code base). This means that the users keys are encrypted by the user's Web2 authentication method. The user could lose access to "their" Hive Lite Account if:
Their Web2 account is compromised
LeoInfra is compromised
The passthrough of their keys to LeoInfra is compromised (man-in-the-middle attacks)
*"their" is in parentheses as both you as the app owner and the user should be aware that the account has very low security (as low or worse than a Web2 sign in method). INLEO's use of Lite Accounts on our frontend gives a disclaimer to the user that they are using a temporary account that doesn't belong to them. In order to take control of the account, they need to change and download their keys - our UI has a Lite Account to Full Account flow where all of the keys get changed and downloaded by the user so that they can safely take custody of the "temporary" account they are using. We cannot stress the LOW SECURITY nature of Lite Accounts enough. While they make it easy and convenient to sign up a new user, users should be continuously reminded that they don't own the Hive account they're controlling with their Web2 account.
Use of Lite Accounts is meant to be a temporary means of signing users up. We consider them to be a low security signup method that is extremely convenient but also risky in terms of the security of the account. For this reason, when a user is signed up, they are given ample warnings and if they get active on INLEO, we continually pester them to follow our flow and convert their account to a Full Hive Account. If you operate a Hive UI and choose to integrate this sign up method, we recommend considering certain disclaimer displays that we have created (such as restrictions when a user starts depositing funds - telling them they MUST go full self-custody to continue, etc.):
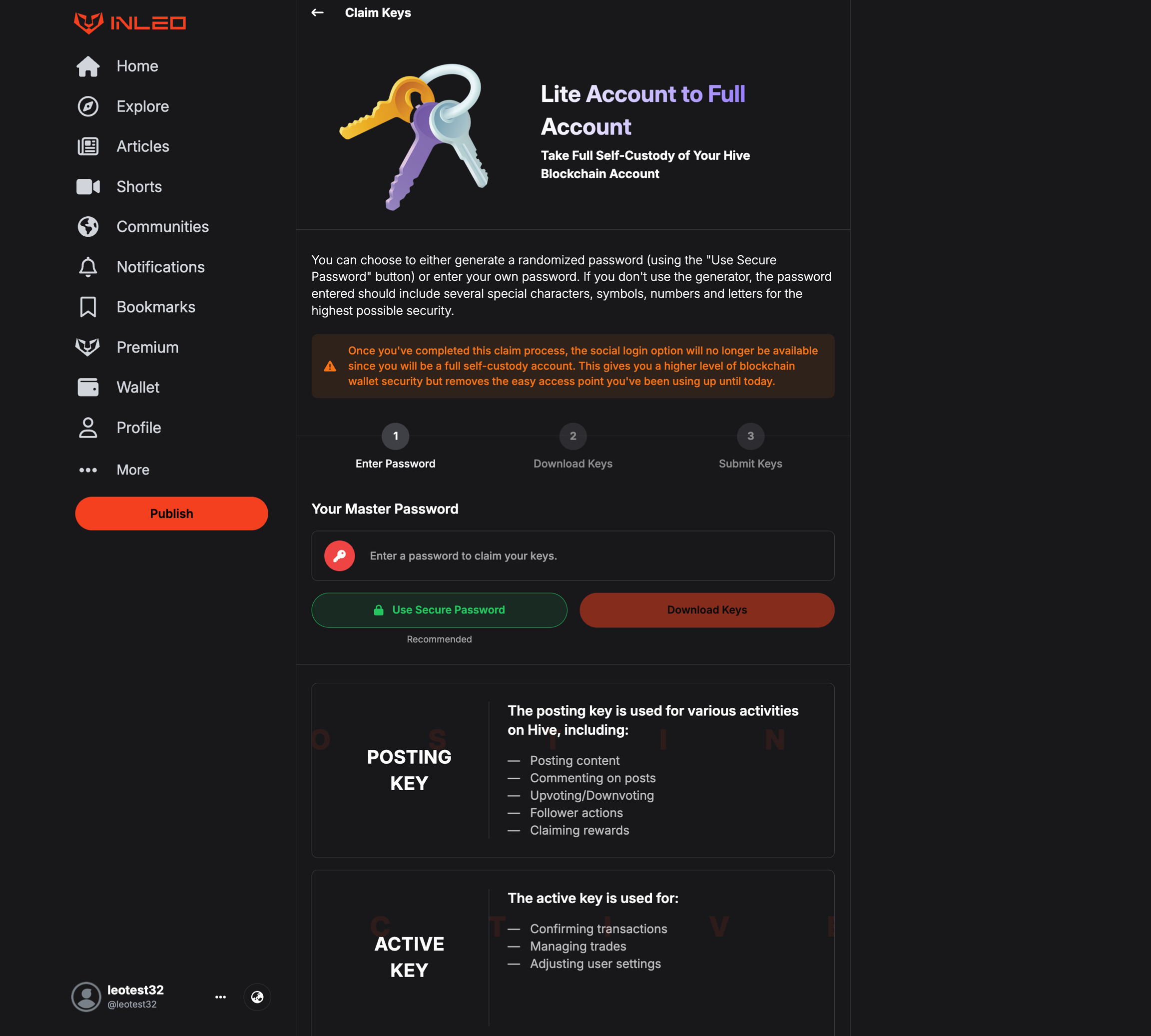
For this reason, we have ample disclaimers on INLEO's frontend - and recommend all frontends who add similar disclaimers if they choose to integrate Lite Accounts. Including ones based on the crypto held in a Lite Account. After a Lite Account reaches more than $1 on it, our UI starts warning them that their funds aren't fully secure until they take Full Self Custody. A link to our docs explains it in more detail.
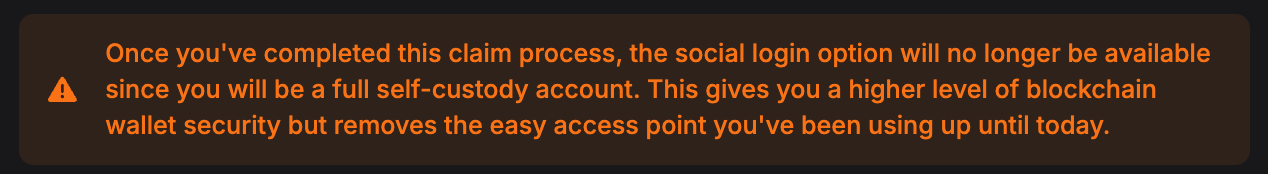
Lite Accounts offer full access to Hive services but do so with a massive security trade-off. We developed Lite Accounts so that new users could quickly and easily sign up to Hive and start using the ecosystem. Once that user has familiarized themself with the ecosystem, they are bombarded with messages from us to "Take Full Self Custody" of their account.
When a Lite Account user is on INLEO, there is persistent messaging to remind them that they're on a Lite Account and we recommend taking Full Self-Custody. On this messaging, there is an action button. This button takes them to a page on INLEO where there is a simple and easy-to-use flow that:
Changes their Hive Private Keys
Downloads the new Keys
This allows them to turn a Lite Account into a full, self-custodied Hive Account. The keys are changed so that the encrypted keys in LeoInfra are no longer usable and the user is the only one with the new copy of their Hive Account Keys.
1. Signup a User With Firebase (Lite Account)
To sign a user up for Hive using our Lite Account method and our resources, use the following steps. REMINDER (yes, we can't stress this enough): a Lite account should be viewed and explained to the user as essentially a temporary account that they do not own. They only truly own the account when they take full self-custody. If you implement the following, ensure your UI has ample disclaimers and education around this.
they need to implement firebase sdk into their ui need us to allow their domain for firebase logins they need to request client key + domain allowance from us for keystore
Create a new Hive account using Firebase authentication.
URL: https://inleo.io/leoinfra/auth/signup
Method: POST
Content-Type: application/json
Description: Registers a new user with Firebase credentials and creates a Hive account.
Request Payload
username: Desired Hive username (must be unique).firebase_uid: User's Firebase UID.firebase_id_token: Token from Firebase authentication.memo_key: Public memo key for the Hive account.public :Public keys (posting, owner, active) for the Hive account.referral: Optional referral username.
Firebase SDK + Whitelisting
You will also need to implement the firebase SDK into your UI.
The final step is to reach out to the INLEO team (contact info above) and we will whitelist your app's domain.
If you want to fork the codebase and run your own instance of LeoInfra, this section covers the documentation for that. Please refer to the Disclaimers section above about how LeoInfra works and how you should protect yourself and your users (especially with Lite Accounts) using ample disclaimer displays and user flows for taking full self-custody before a user starts earning/depositing on their account.
Again: Lite Accounts are not meant to be a long-term sign-in option. Your frontend cannot stress this enough.
Endpoints
1. Signup User with Firebase
Create a new Hive account using Firebase authentication.
URL: /auth/signup
Method: POST
Content-Type: application/json
Description: Registers a new user with Firebase credentials and creates a Hive account.
Request Payload
username: Desired Hive username (must be unique).firebase_uid: User's Firebase UID.firebase_id_token: Token from Firebase authentication.memo_key: Public memo key for the Hive account.public :Public keys (posting, owner, active) for the Hive account.referral: Optional referral username.
Potential Responses
Success (200 OK):
Failure (200 OK):
How to Use
Obtain a Firebase ID token by authenticating with Firebase (e.g., via their SDK).
Generate or provide Hive public keys (e.g., using a tool like Hive Keychain).
Send a POST request with the payload above using a tool like
curlor Postman:
Check the response for success or error messages
Last updated